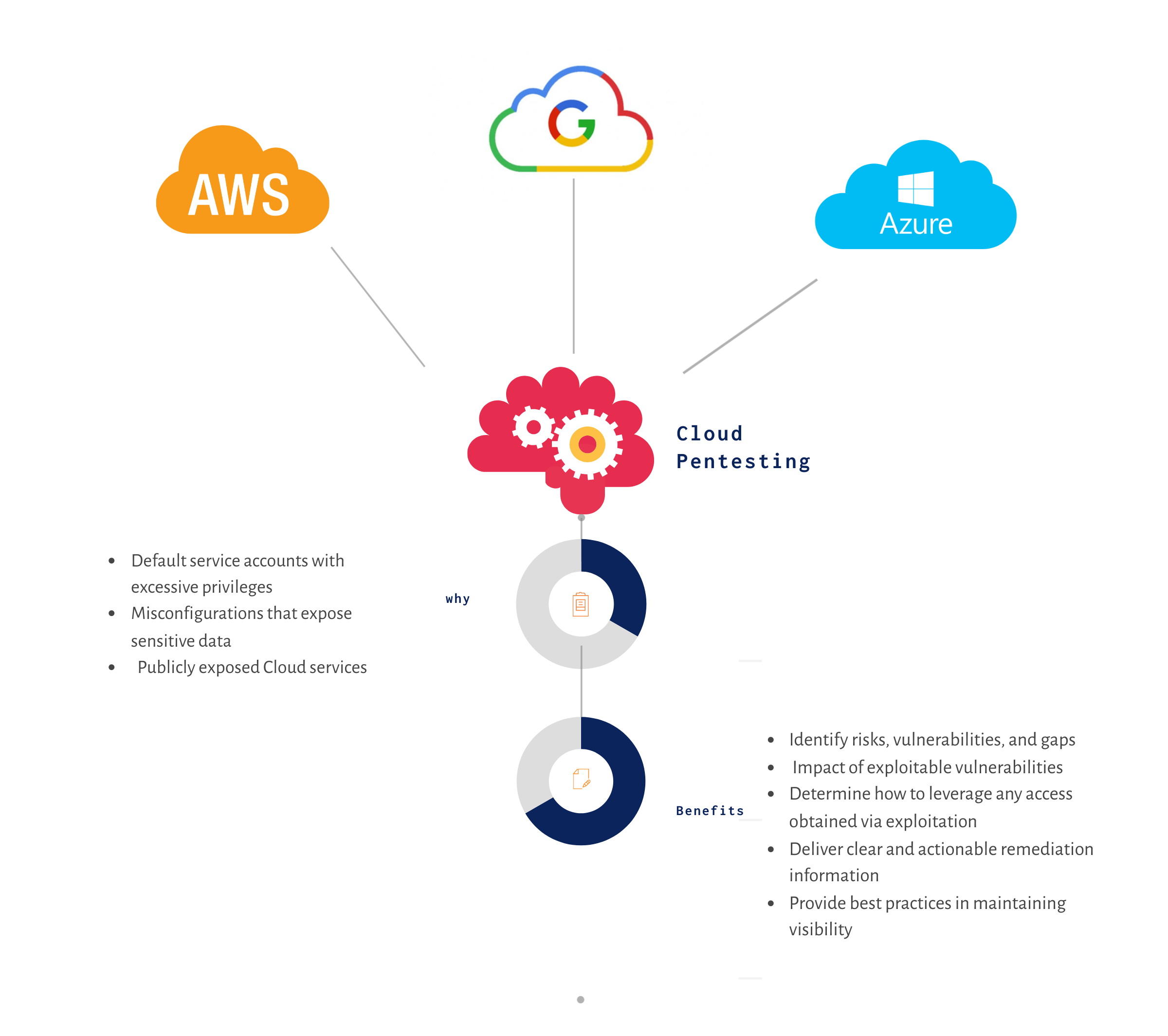
The Importance and benefits of Cloud Penetration Testing.
Many organizations have adopted cloud computing for the delivery of computing services as it offers flexible resources, economies of scale & faster innovation. While the cloud offers many advantages, it also opens the doors to a few challenges.
The major challenge faced when we use cloud infrastructures is that every cloud provider will have their proprietary security policies and controls and the teams have to configure and secure the different cloud environments which often leads to misconfigurations and opens the door for security breaches.
So as to consistently check for the health of cloud infrastructures it is recommended to have periodic penetration testing done. Organizations may strengthen their cloud security overall and prevent breaches by using cloud penetration testing.
Additionally, enterprises will have a more thorough picture of their cloud assets, including how attack-resistant and vulnerable the present cloud security is.Cloud Pentesting is performed under strict guidelines from the cloud service providers in order to find and exploit security flaws. A Cloud Penetration test simulates a controlled cyber-attack on your cloud infrastructure.
Different types of Cloud Penetration Testing:
Cloud Penetration Testing examines issues relating to attack, breach, operability, and recovery within a cloud environment.
Black Box Penetration Testing— The Cloud Penetration testers are unfamiliar with and have no prior access to your cloud systems throughout this assault simulation.
Grey Box Penetration Testing— Cloud Penetration testers may be given restricted administrative rights and have limited user and system expertise.
White Box Penetration Testing— Root-level access to cloud systems is available to Cloud Penetration testers.
Types of common Cloud Penetration testing:
- AWS Penetration Testing
- Google Cloud Penetration Testing
- Microsoft Azure Penetration Testing
- Docker and Kubernetes Penetration Testing
- Containers Penetration Testing
Microsoft: https://www.microsoft.com/en-us/msrc/pentest-rules-of-engagement
Aws Amazon: https://aws.amazon.com/security/penetration-testing/
Google cloud platform: https://support.google.com/cloud/answer/6262505?hl=en
Cloud security threats can be prevented with Cloud Penetration Testing:
Insecure APIs:
Cloud Penetration Testing services make full use of the APIs to distribute vital information among several apps. Additionally, improperly using HTTP techniques in APIs, such as PUT, POST, Remove, etc., might allow hackers to upload malicious code or other information to your server and delete, edit, modify, or hijack the database without your consent.
Cloud Server Misconfigurations:
Misconfiguration is now the most widespread cloud vulnerability, particularly when it comes to S3 buckets. Inappropriate allotments, which result in not encrypting the databases and failing to discriminate between private and public information, are the most common cloud server configuration errors.
Weak Credentials:
If you use the most popular or weak passwords for your cloud accounts, you might undoubtedly become subject to cyber-attacks utilising them, such as those used in brute force assaults. The threat actor with malicious intent may skilfully automate a number of tools to make educated guesses of any strings of potential passwords, opening the door for your regular accountant to use those credentials.
These sorts of cyber-attacks frequently occur when users try to reuse passwords or use passwords that are simple to remember. This scenario may be regularly tested during cloud penetration testing.
Outdated Software:
Working with out-of-date software versions can potentially have horrifying outcomes since they are quite susceptible to possible hazards that the corporation has already addressed in the most recent software version.
Most software providers do not plan to employ an effective update system, or users themselves turn off automatic updates, preventing them from being updated and clogging up storage with meaningless data.
For a long-term, safe and sound working approach, one only needs to upgrade their working programme to the most recent version.
Insecure Coding Practices:
Businesses constantly work to reduce the cost of their cloud infrastructure often employ subpar coding to minimise costs and thus invite flaws like SQLi, XSS, CSRF, etc. The OWASP Top 10 list includes the vulnerabilities that are the most prevalent among them. As a result, the primary reason why so many cloud computing services have been compromised is due to these vulnerabilities.
Conclusion:
The purpose of Cloud Penetration Testing is to examine issues relating to attack, breach, operability, and recovery within a cloud environment. Cloud Penetration Testing simulates a controlled cyber-attack on your cloud infrastructure. Cloud Penetration Testing services make full use of the APIs to distribute vital information among several apps. improperly using HTTP techniques in APIs, such as PUT, POST, Remove, etc., might allow hackers to upload malicious code or other information to your server.The OWASP Top 10 list includes the vulnerabilities that are the most prevalent among them. As a result, working with out-of-date software can potentially have horrifying outcomes. For a long-term safe and sound working approach, one only needs to upgrade their working program to the most recent version. These types of cloud security threats can be prevented with Cloud Penetration Testing.